All Categories
Featured
Table of Contents
The cash money conversion cycle (CCC) is among a number of procedures of monitoring effectiveness. It measures just how fast a business can convert cash money accessible right into a lot more money available. The CCC does this by following the cash, or the capital expense, as it is first exchanged supply and accounts payable (AP), via sales and accounts receivable (AR), and afterwards back into cash.

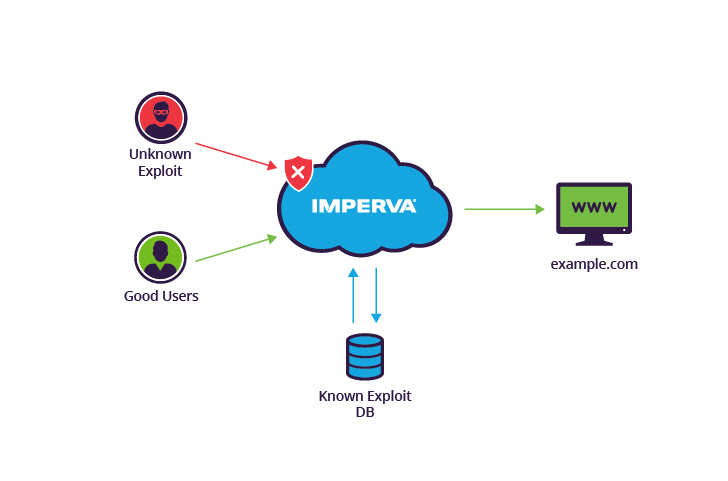
A is the usage of a zero-day exploit to cause damage to or take data from a system affected by a vulnerability. Software program often has safety and security vulnerabilities that hackers can manipulate to trigger chaos. Software developers are always keeping an eye out for susceptabilities to "spot" that is, develop a remedy that they release in a brand-new upgrade.
While the susceptability is still open, assaulters can write and execute a code to capitalize on it. This is called exploit code. The make use of code may result in the software individuals being taken advantage of as an example, with identity theft or other kinds of cybercrime. When opponents identify a zero-day susceptability, they require a means of reaching the susceptible system.
What Does Banking Security Mean?
Safety and security susceptabilities are commonly not found straight away. It can sometimes take days, weeks, and even months before programmers determine the vulnerability that caused the attack. And even once a zero-day spot is launched, not all customers fast to implement it. In recent times, cyberpunks have been much faster at exploiting susceptabilities right after discovery.
: cyberpunks whose motivation is normally financial gain hackers motivated by a political or social reason that desire the strikes to be visible to attract attention to their cause cyberpunks who spy on companies to obtain information about them nations or political stars snooping on or assaulting one more country's cyberinfrastructure A zero-day hack can make use of susceptabilities in a selection of systems, consisting of: As an outcome, there is a broad array of prospective victims: Individuals that make use of a prone system, such as a browser or running system Cyberpunks can make use of protection susceptabilities to jeopardize devices and build big botnets People with accessibility to important business data, such as intellectual residential or commercial property Hardware gadgets, firmware, and the Net of Points Big companies and companies Government firms Political targets and/or national safety and security threats It's useful to assume in regards to targeted versus non-targeted zero-day strikes: Targeted zero-day assaults are performed against potentially beneficial targets such as huge organizations, government firms, or top-level people.
This website uses cookies to help personalise content, tailor your experience and to maintain you visited if you register. By continuing to use this website, you are consenting to our use cookies.
9 Easy Facts About Banking Security Shown
Sixty days later is typically when a proof of concept emerges and by 120 days later on, the susceptability will be consisted of in automated susceptability and exploitation devices.
However before that, I was just a UNIX admin. I was considering this concern a great deal, and what happened to me is that I do not recognize as well many individuals in infosec who chose infosec as a profession. The majority of the individuals who I know in this area didn't go to college to be infosec pros, it simply type of occurred.
Are they interested in network security or application protection? You can obtain by in IDS and firewall globe and system patching without recognizing any kind of code; it's fairly automated stuff from the product side.
5 Easy Facts About Security Consultants Described
So with equipment, it's much various from the job you make with software application protection. Infosec is an actually big area, and you're mosting likely to have to select your particular niche, because no person is mosting likely to be able to connect those spaces, at the very least efficiently. Would certainly you say hands-on experience is extra essential that official protection education and learning and accreditations? The inquiry is are individuals being employed into entry degree safety and security settings right out of school? I assume somewhat, yet that's most likely still pretty rare.
I think the universities are simply now within the last 3-5 years obtaining masters in computer protection scientific researches off the ground. There are not a lot of trainees in them. What do you believe is the most vital certification to be successful in the safety and security space, no matter of a person's background and experience level?
And if you can understand code, you have a much better probability of having the ability to recognize exactly how to scale your solution. On the defense side, we're out-manned and outgunned frequently. It's "us" versus "them," and I do not recognize the amount of of "them," there are, however there's going to be as well few of "us "in any way times.
The smart Trick of Banking Security That Nobody is Talking About
As an example, you can envision Facebook, I'm not certain many security people they have, butit's mosting likely to be a tiny portion of a percent of their individual base, so they're going to need to find out exactly how to scale their solutions so they can safeguard all those individuals.
The scientists saw that without understanding a card number beforehand, an assailant can introduce a Boolean-based SQL injection via this area. Nevertheless, the data source responded with a 5 2nd hold-up when Boolean true declarations (such as' or '1'='1) were provided, resulting in a time-based SQL injection vector. An assailant can utilize this technique to brute-force query the data source, enabling info from available tables to be revealed.
While the information on this implant are scarce at the minute, Odd, Job functions on Windows Server 2003 Business up to Windows XP Expert. A few of the Windows ventures were also undetected on online file scanning service Infection, Total, Safety Designer Kevin Beaumont confirmed via Twitter, which indicates that the devices have actually not been seen prior to.
Latest Posts
Plumbing around Tucson
24/7 Plumbing around Tucson
24/7 Plumbing around Tucson, California